The Internet of Things (IoT) may encompass an ever-expanding array of devices, but it revolves around one mission: making life connected. Whether modernizing industrial applications, transforming consumer relationships with technology in the smart home, or constructing buildings and cities to be more efficient, IoT and digital transformation are optimizing everyday life and helping the world run more smoothly.
But this connectivity shouldn’t come at a cost. There’s a significant danger that the rapid pace of IoT advancement is potentially outstripping the development of the IoT security infrastructure. Optimization shouldn’t mean easy access for criminals, while convenience isn’t worth sacrificing security. Below, we delve into the history of IoT security, from how the IoT started life as a disparate array of ideas, to how it has grown to transform industries and make all our lives easier. As with any emerging technology, it’s not always been easy, it brings with it challenges that only collaboration can resolve.
A Brief History of the IoT
1832
The Internet of Things may sound like a recent phenomenon but its roots can be traced back to the 19th Century. In fact, the concept of connected devices dates back to 1832, when Baron Schilling designed the first electromagnetic telegraph that allowed direct communication between two machines through the transfer of electrical signals. It’s this Machine-to-Machine (M2M) communication that laid the groundwork for the growth of IoT
1970s
However, it wasn’t until the 1970s that technology had advanced to allow M2M and connected devices to really start to take shape. The rapid development of M2M in this decade led to the emergence of early IoT devices that, true to IoT’s mission, were born out of a desire to make life simpler.
1982

For example, in 1982, a group of students at Carnegie Melon University invented one of the earliest known connected devices to monitor the contents of a Coca-Cola vending machine and save themselves a walk if they knew it was empty.
1989
Of course, it was the emergence of the World Wide Web, proposed by Tim Berners-Lee in 1989, that finally put the internet in the Internet of Things. A year later, John Romkey put this to the test and created a toaster that could be turned on and off via the Internet.
1992
IoT is capable of many things, from making the consumer’s life simpler to transforming a wide range of industries, including manufacturing. The IIoT journey can be seen to start in 1992 when programmable logic controllers (PLCs) gained connectivity. Since that time, they have been central to the development and use of automated assembly lines and industrial robots in factories.
1993
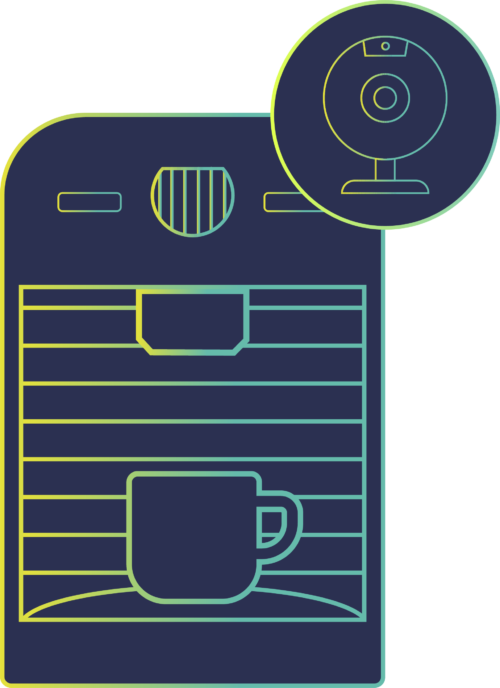
Early examples of IoT design were based around convenience, or simply as a way of proving they could be done. For example, in 1993, scientists at the University of Cambridge created what is believed to be the first ‘webcam’, designed to report on the fullness of a coffee pot so that they didn’t have to go and check it for themselves.
1994
The concept of smart cities may sound like something out of a novel, but they too have long been a part of the IoT vision. IoT devices such as connected sensors, lights, and meters that collect and analyze data improve our cities’ infrastructure, public services, and more. In 1994, Amsterdam created arguably the first smart city with a virtual ‘digital city’, De Digitale Stad, to promote internet use.

1999

Although we’ve already seen a number of examples of connected devices in action, it wasn’t until 1999 that the term “Internet of Things” was first coined. It is said to have been introduced by Kevin Ashton, the Executive Director of Auto-ID Labs at MIT when he wanted to attract attention to a new exciting technology called RFID.
2008
IoT development was taken to another level with the advent of cloud computing in the early 2000s that enabled the network of connectivity we exist in today. Fast forward to 2008 and the number of total connected devices in the world had already overtaken the global population.
2010s
While the concept of IoT really started to take off in the 2010s, this period also showed us how an increasing network of connected devices also means an increasingly attractive, large target for cybercriminals. IoT security started to become a critical issue for governments, businesses and individual users.
2016
Arguably one of the most famous hacks of all time, the Mirai Botnet hack was a huge denial of service attack (DDoS) making use of Internet of Things devices. The hackers used default passwords to access services and spread malware into connected devices.
2017
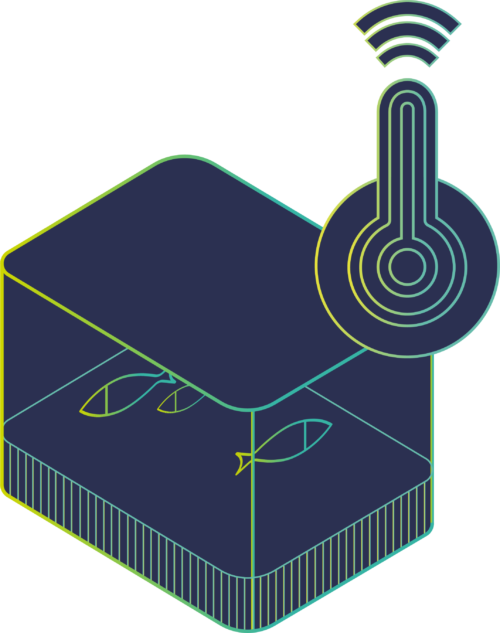
The infamous SUV hack from 2017 – where a team of researchers exploited an update vulnerability to remotely hijack a vehicle and control its speed and direction – shows that single users can be strategically targeted. And we know that hackers are constantly looking for new ways to access people’s data. In 2017 they used an unconventional method to break into a casino, accessing its network via an internet-connected thermometer in a fish tank to extract its database.
2019
In February 2019, Arm’s PSA architecture specification expands to become an architecture agnostic certification scheme. PSA Certified launches as a purpose-built scheme for connected IoT devices to have their security credentials validated.
Early movers start to closely consider IoT security, looking at certification of connected devices, based on standards such as NIST, ETSI and UK DCMS.
2022
The industry had been anticipating the launch of security regulation for a long time, and in 2022 that prediction became a reality. Governments start to consider their regulation efforts for improving the quality of security in devices, the EU announce the proposed European Cyber Resilience Act in October 2022.
CENELEC announce that Radio Equipment Directive (RED) will extend to apply to wireless connected devices from August 2024.
2023
In August 2023, The White House announces the creation of a voluntary, consumer facing security label – the US Cyber Trust Mark. Consumer demand for security reaches an all-time high, the PSA Certified 2023 Security Report found that 65% of consumers say they value or look for security credentials when buying connected products as a consumer, while 69% are happy to pay a premium for them.
PSA Certified and the Future of IoT Security
We’ve seen from our exploration of key moments in the history of IoT, that with its rapid development, security has often been an afterthought, or in some cases, not thought of at all!
Fear shouldn’t stop organizations from embracing the benefits of IoT. But it should make them think carefully about the way they’re protecting networks and devices. The future is connected – it’s estimated that there will be 9.27 connected devices per person by 2025 – and clearly it’s imperative that those devices should be secure.
PSA Certified was developed to provide the much-needed global security structure for connected devices. In 2017, Arm introduced Platform Security Architecture (PSA) to transform embedded IoT security and in 2019 this evolved to become PSA Certified: a collaboration between seven expert security companies.
Since then, we have launched a series of security certifications, for silicon vendors, system software providers, and devices, helping companies create innovative new technology that doesn’t create IoT weak links. The PSA Certified scheme has scaled to become one of the fastest growing, most valued security ecosystems, globally. With over 170 certifications from over 80 partners, PSA Certified has democratized the adoption of security across the electronics industry, giving the ecosystem the confidence to innovate, while protecting consumers, businesses, and service providers from the most common hacks.

